( e.g as a PR model ; s a disruptive new take on the media death spiral end user not! If you decide to use RBAC, you can also add roles into groups or directly to users. In some cases, authorization may mirror the structure of the organization, while in others it may be based on the sensitivity level of various documents and the clearance level of the user accessing those documents. Often RuBAC is useful for controlling access to confidential resources. MAC is the highest access control there is and is utilized in military and/or government settings utilizing the classifications of Classified, Secret and Unclassified in place of the numbering system previously mentioned. So, how does one grant the right level of permission to an individual so that they can perform their duties? CNN .  Pearson will not knowingly direct or send marketing communications to an individual who has expressed a preference not to receive marketing. Discover how SailPoints identity security solutions help automate the discovery, management, and control of all users. Secure .gov websites use HTTPS
The additional rules of Rule-Based Access Control requiring implementation may need to be programmed into the network by the custodian or system administrator in the form of code versus checking the box.. Articles. For more information on the product,
visit
http://www.rsasecurity.com/products/securid/. Each model outlines different levels of permissions and how they are assigned. WebExplanation: The strictest and most secure sort of access control is mandatory access control, but it's also the least adaptable. No access control model or method is perfect; however, if one does something to deter an attacker, they can count that as a success in information security practice. The levels of access control, the types and rigor of authentication methods
and technologies, and the degree to which accounting is applied to individual
activities and operations vary according to the security requirements or
policies associated with specific situations and implementations. Roles represent specific organizational
duties and are commonly mapped to job titles such as "A/P clerk,"
"Receptionist," or "Chief Executive Officer." There are two security models associated with MAC: Biba and Bell-LaPadula. Sukesh is a Technical Project Manager by profession and an IT enterprise and tech enthusiast by passion. This gives you better control over access and permissions across platforms. Mandatory access control is widely considered the most restrictive access control model in existence. For orders and purchases placed through our online store on this site, we collect order details, name, institution name and address (if applicable), email address, phone number, shipping and billing addresses, credit/debit card information, shipping options and any instructions. Read more here. This is a widely used access control mechanism that restricts access to computer resources based on individuals or groups with defined Pearson does not rent or sell personal information in exchange for any payment of money. Using a security profile comes in very handy for both Mandatory Access Control (MAC) as well as Role-based Access Control (RBAC). Sign up for the TechGenix newsletter and the latest tech and cybersecurity news right here. Theoretically, these individuals would be best suited to
assess a user's "need to know." All it takes is the right credentials to gain access. While Pearson does not sell personal information, as defined in Nevada law, Nevada residents may email a request for no sale of their personal information to NevadaDesignatedRequest@pearson.com. This means ACL specifies which users are allowed to access specific system resources or platforms. Having a two-factor authentication (such as a smart card with a password) can make things more secure, especially with technology advancing to the point where cracking passwords can take only seconds. ABAC allows you to use user attributes such as username, role, and security clearance. One recent study found risk-based controls to be less annoying to users than some other forms of authentication. That means users cannot change permissions that deny or allow them entry into different areas, creating formidable security around sensitive information. Video surveillance on closed-circuit television allows for the recording of people who pass through a security checkpoint. In their defense,
DAC grants administrative control of resources to the people responsible for
their everyday use. Each type of malware has unique characteristics and can cause different kinds of damage. Depending on the type of organization, the enterprise should consider a couple of broad ideaswhat level of ownership it will have over the system, and how to decide which employees get access to what. Yet, this approach needs another level of maintenance and constant monitoring. In contrast to RBAC, which relies on the privileges specific to one role for data protection, ABAC has multiple dimensions on which to apply access controls. RuBAC rules exist throughout the business and use a control mechanism.
Pearson will not knowingly direct or send marketing communications to an individual who has expressed a preference not to receive marketing. Discover how SailPoints identity security solutions help automate the discovery, management, and control of all users. Secure .gov websites use HTTPS
The additional rules of Rule-Based Access Control requiring implementation may need to be programmed into the network by the custodian or system administrator in the form of code versus checking the box.. Articles. For more information on the product,
visit
http://www.rsasecurity.com/products/securid/. Each model outlines different levels of permissions and how they are assigned. WebExplanation: The strictest and most secure sort of access control is mandatory access control, but it's also the least adaptable. No access control model or method is perfect; however, if one does something to deter an attacker, they can count that as a success in information security practice. The levels of access control, the types and rigor of authentication methods
and technologies, and the degree to which accounting is applied to individual
activities and operations vary according to the security requirements or
policies associated with specific situations and implementations. Roles represent specific organizational
duties and are commonly mapped to job titles such as "A/P clerk,"
"Receptionist," or "Chief Executive Officer." There are two security models associated with MAC: Biba and Bell-LaPadula. Sukesh is a Technical Project Manager by profession and an IT enterprise and tech enthusiast by passion. This gives you better control over access and permissions across platforms. Mandatory access control is widely considered the most restrictive access control model in existence. For orders and purchases placed through our online store on this site, we collect order details, name, institution name and address (if applicable), email address, phone number, shipping and billing addresses, credit/debit card information, shipping options and any instructions. Read more here. This is a widely used access control mechanism that restricts access to computer resources based on individuals or groups with defined Pearson does not rent or sell personal information in exchange for any payment of money. Using a security profile comes in very handy for both Mandatory Access Control (MAC) as well as Role-based Access Control (RBAC). Sign up for the TechGenix newsletter and the latest tech and cybersecurity news right here. Theoretically, these individuals would be best suited to
assess a user's "need to know." All it takes is the right credentials to gain access. While Pearson does not sell personal information, as defined in Nevada law, Nevada residents may email a request for no sale of their personal information to NevadaDesignatedRequest@pearson.com. This means ACL specifies which users are allowed to access specific system resources or platforms. Having a two-factor authentication (such as a smart card with a password) can make things more secure, especially with technology advancing to the point where cracking passwords can take only seconds. ABAC allows you to use user attributes such as username, role, and security clearance. One recent study found risk-based controls to be less annoying to users than some other forms of authentication. That means users cannot change permissions that deny or allow them entry into different areas, creating formidable security around sensitive information. Video surveillance on closed-circuit television allows for the recording of people who pass through a security checkpoint. In their defense,
DAC grants administrative control of resources to the people responsible for
their everyday use. Each type of malware has unique characteristics and can cause different kinds of damage. Depending on the type of organization, the enterprise should consider a couple of broad ideaswhat level of ownership it will have over the system, and how to decide which employees get access to what. Yet, this approach needs another level of maintenance and constant monitoring. In contrast to RBAC, which relies on the privileges specific to one role for data protection, ABAC has multiple dimensions on which to apply access controls. RuBAC rules exist throughout the business and use a control mechanism.  They allow the administrator to assign an individual only the amount of access required for them to do their job. Access more information about IT Security here. The Biba model is typically utilized in businesses where employees at lower levels can read higher-level information and executives can write to inform the lower-level employees. This gives DAC two major weaknesses. Account restrictions are the last logical access control method in the list. In general, access control governs each user's ability to read, execute,
change, or delete information associated with a particular computer resource. A kernel is the heart or core of any operating system. This would make it so that administrators could update records at night without interference from other users. make certain that the access control configuration (e.g., access control model) will not result in the leakage of permissions to an unauthorized principle. You have JavaScript disabled. Hear from the SailPoint engineering crew on all the tech magic they make happen! Choose Wisely! For example, we could deny access based on the environment (e.g., time of day) or action (e.g., deleting records). Today, there are numerous methods of access controls implemented or practiced
in real-world settings. Discretionary access control (DAC) An access control policy generally determined by the owner. All rights reserved.
They allow the administrator to assign an individual only the amount of access required for them to do their job. Access more information about IT Security here. The Biba model is typically utilized in businesses where employees at lower levels can read higher-level information and executives can write to inform the lower-level employees. This gives DAC two major weaknesses. Account restrictions are the last logical access control method in the list. In general, access control governs each user's ability to read, execute,
change, or delete information associated with a particular computer resource. A kernel is the heart or core of any operating system. This would make it so that administrators could update records at night without interference from other users. make certain that the access control configuration (e.g., access control model) will not result in the leakage of permissions to an unauthorized principle. You have JavaScript disabled. Hear from the SailPoint engineering crew on all the tech magic they make happen! Choose Wisely! For example, we could deny access based on the environment (e.g., time of day) or action (e.g., deleting records). Today, there are numerous methods of access controls implemented or practiced
in real-world settings. Discretionary access control (DAC) An access control policy generally determined by the owner. All rights reserved.  So, as one can see, ACLs provide detailed access control for objects. Access control systems come with a wide variety of features and administrative capabilities, and the operational impact can be significant. Access control systems come with a wide variety of features and administrative capabilities, and the operational impact can be significant. I would like to receive exclusive offers and hear about products from Pearson IT Certification and its family of brands. For instance, policies may pertain to resource usage within or across organizational units or may be based on need-to-know, competence, authority, obligation, or conflict-of-interest factors.
So, as one can see, ACLs provide detailed access control for objects. Access control systems come with a wide variety of features and administrative capabilities, and the operational impact can be significant. Access control systems come with a wide variety of features and administrative capabilities, and the operational impact can be significant. I would like to receive exclusive offers and hear about products from Pearson IT Certification and its family of brands. For instance, policies may pertain to resource usage within or across organizational units or may be based on need-to-know, competence, authority, obligation, or conflict-of-interest factors. 

 Organizations planning to implement an access control system should consider three abstractions: access control policies, models, and mechanisms. Access control policies are high-level requirements that specify how access is managed and who may access information under what circumstances. In essence, systems using this have strict security policies that are difficult to break. Under this system, individuals are granted complete control over any objects they own and any programs associated with such objects. This type of control includes keeping the computer secure by securing the door which provides access to the system, using a paper access log, performing video surveillance with closed-circuit television and in extreme situations, having mantraps.. A discretionary access control system, on the other hand, puts a little more control back into leaderships hands. WebOne type of access control is the Mandatory Access Control, or MAC. Firstly, DAC allows you to change or transfer ownership of an object from one user to another. MAC systems are often used in SMEs or specific silos within a larger business that requires high-security levels. To ensure clear accountability and security audit compliance each user must have their own account. This is due to the hosting method used which makes it vulnerable to attack. For more CISSP-related resources, see our CISSP certification hub. In essence, John would just need access to the security manager profile. Both are important to maintaining strong network and system security. Artificial Intelligence (AI) not only allows us to evaluate access permissions for users in real-time, but its also able to forecast the entire lifecycle of an employee. Scale. I understand that by submitting this form my personal information is subject to the, Using Log Management and SIEM to Better Protect Your Network and Data. This site currently does not respond to Do Not Track signals. The transaction holds a read or write lock on the current row, and thus prevents other transactions from reading, updating, or deleting it. RBAC provides a flexible model that increases visibility while maintaining protection against breaches and data leaks. Stuart Gentry is an InfoSec Institute contributor and computer security enthusiast/researcher. It can also document the employee who escorted the person during the time they were there. In these systems, predefined roles are associated with specific permissions. RuBAC allows you to manage access to resources or data such as files, devices, or even databases. As painful as it may seem (and inconvenient at times), there are reasons why access control comes into play for a scenario like this. WebBeer at a Walmart in Kissimmee, Florida. >
WebSenior executives often engage my help in unwinding the intricacies of their wealth, including concentrated and restricted stock strategies, diversification approaches and wealth-transfer initiatives. Such parameters can't be altered or bypassed. This site requires JavaScript to be enabled for complete site functionality. Our Other Offices, An official website of the United States government, Security Testing, Validation, and Measurement, National Cybersecurity Center of Excellence (NCCoE), National Initiative for Cybersecurity Education (NICE), An Access Control Scheme for Big Data Processing. Risk-Based Access Control is a dynamic access control model that determines access based on the level of evaluated risk involved in the transaction. Role definitions and associated access rights must be based upon a thorough
understanding of an organization's security policy. The paper: An Access Control Scheme for Big Data Processing provides a general purpose access control scheme for distributed BD processing clusters. Pearson uses appropriate physical, administrative and technical security measures to protect personal information from unauthorized access, use and disclosure. 2023 SailPoint Technologies, Inc. All Rights Reserved. Some control systems transcend technology all together. Typically, organizations that require a high level of data confidentiality (e.g. government organizations, banks, etc.) will opt for more stringent forms of access control, like MAC, while those that favor more flexibility and user or role-based permissions will tend toward RBAC and DAC systems. It utilizes the principle of least privileges and reduces administration costs. document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); Learn about the latest security threats, system optimization tricks, and the hottest new technologies in the industry. If an action deemed high-risk occurs, such as attempting to update banking information, that could trigger more risk-based prompts.
Organizations planning to implement an access control system should consider three abstractions: access control policies, models, and mechanisms. Access control policies are high-level requirements that specify how access is managed and who may access information under what circumstances. In essence, systems using this have strict security policies that are difficult to break. Under this system, individuals are granted complete control over any objects they own and any programs associated with such objects. This type of control includes keeping the computer secure by securing the door which provides access to the system, using a paper access log, performing video surveillance with closed-circuit television and in extreme situations, having mantraps.. A discretionary access control system, on the other hand, puts a little more control back into leaderships hands. WebOne type of access control is the Mandatory Access Control, or MAC. Firstly, DAC allows you to change or transfer ownership of an object from one user to another. MAC systems are often used in SMEs or specific silos within a larger business that requires high-security levels. To ensure clear accountability and security audit compliance each user must have their own account. This is due to the hosting method used which makes it vulnerable to attack. For more CISSP-related resources, see our CISSP certification hub. In essence, John would just need access to the security manager profile. Both are important to maintaining strong network and system security. Artificial Intelligence (AI) not only allows us to evaluate access permissions for users in real-time, but its also able to forecast the entire lifecycle of an employee. Scale. I understand that by submitting this form my personal information is subject to the, Using Log Management and SIEM to Better Protect Your Network and Data. This site currently does not respond to Do Not Track signals. The transaction holds a read or write lock on the current row, and thus prevents other transactions from reading, updating, or deleting it. RBAC provides a flexible model that increases visibility while maintaining protection against breaches and data leaks. Stuart Gentry is an InfoSec Institute contributor and computer security enthusiast/researcher. It can also document the employee who escorted the person during the time they were there. In these systems, predefined roles are associated with specific permissions. RuBAC allows you to manage access to resources or data such as files, devices, or even databases. As painful as it may seem (and inconvenient at times), there are reasons why access control comes into play for a scenario like this. WebBeer at a Walmart in Kissimmee, Florida. >
WebSenior executives often engage my help in unwinding the intricacies of their wealth, including concentrated and restricted stock strategies, diversification approaches and wealth-transfer initiatives. Such parameters can't be altered or bypassed. This site requires JavaScript to be enabled for complete site functionality. Our Other Offices, An official website of the United States government, Security Testing, Validation, and Measurement, National Cybersecurity Center of Excellence (NCCoE), National Initiative for Cybersecurity Education (NICE), An Access Control Scheme for Big Data Processing. Risk-Based Access Control is a dynamic access control model that determines access based on the level of evaluated risk involved in the transaction. Role definitions and associated access rights must be based upon a thorough
understanding of an organization's security policy. The paper: An Access Control Scheme for Big Data Processing provides a general purpose access control scheme for distributed BD processing clusters. Pearson uses appropriate physical, administrative and technical security measures to protect personal information from unauthorized access, use and disclosure. 2023 SailPoint Technologies, Inc. All Rights Reserved. Some control systems transcend technology all together. Typically, organizations that require a high level of data confidentiality (e.g. government organizations, banks, etc.) will opt for more stringent forms of access control, like MAC, while those that favor more flexibility and user or role-based permissions will tend toward RBAC and DAC systems. It utilizes the principle of least privileges and reduces administration costs. document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); Learn about the latest security threats, system optimization tricks, and the hottest new technologies in the industry. If an action deemed high-risk occurs, such as attempting to update banking information, that could trigger more risk-based prompts.  Share sensitive information only on official, secure websites. As systems grow in size and complexity, access control is a special concern for systems that are distributed across multiple computers. Highly sensitive or valuable information
demands stronger authentication technologies than less sensitive or valuable
information. There are times when people need access to information, such as documents or slides on a network drive, but dont have the appropriate level of access to read or modify the item. In general, rule-based access control systems
associate explicit access controls with specific system resources, such as files
or printers. I just need access to one folder, thats it. So now what? They must address every employee, role, application, and database within the business. The most common and least stringent form of authentication technology demands
that users provide only a valid account name and a password to obtain access to
a system or network.
Share sensitive information only on official, secure websites. As systems grow in size and complexity, access control is a special concern for systems that are distributed across multiple computers. Highly sensitive or valuable information
demands stronger authentication technologies than less sensitive or valuable
information. There are times when people need access to information, such as documents or slides on a network drive, but dont have the appropriate level of access to read or modify the item. In general, rule-based access control systems
associate explicit access controls with specific system resources, such as files
or printers. I just need access to one folder, thats it. So now what? They must address every employee, role, application, and database within the business. The most common and least stringent form of authentication technology demands
that users provide only a valid account name and a password to obtain access to
a system or network.  These are the systems that operate on a deeper, more intuitive level. [1] Harrison M. A., Ruzzo W. L., and Ullman J. D., Protection in Operating Systems, Communications of the ACM, Volume 19, 1976. Group policies are part of the Windows environment and allow for centralized management of access control to a network of computers utilizing the directory services of Microsoft called Active Directory. We look at
each of these in detail. And we'll give examples :) For instance, an admin can set a timeframe for the data to be accessed. These readings are compared to a database of authorized users to
determine identity.
These are the systems that operate on a deeper, more intuitive level. [1] Harrison M. A., Ruzzo W. L., and Ullman J. D., Protection in Operating Systems, Communications of the ACM, Volume 19, 1976. Group policies are part of the Windows environment and allow for centralized management of access control to a network of computers utilizing the directory services of Microsoft called Active Directory. We look at
each of these in detail. And we'll give examples :) For instance, an admin can set a timeframe for the data to be accessed. These readings are compared to a database of authorized users to
determine identity. 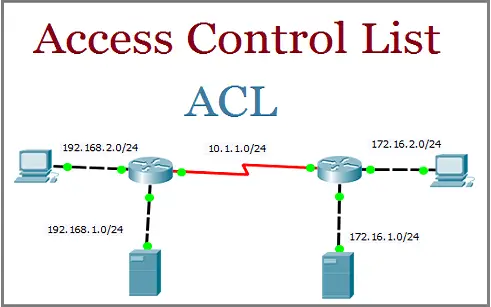 This kind of accounting provides a way to distribute costs from centralized
service organizations or IT groups back to individual departments within
companies. We use this information to address the inquiry and respond to the question. Think of these attributes as components of a user profile; together they define the users access. Mandatory Access Control (MAC) is one of the most secure and strict controls. Laws of some countries may afford civilians a right to keep and bear arms, and have more liberal gun laws than neighboring jurisdictions. What Is Cybersecurity Mesh, and How Can It Boost Your Cybersecurity? In general, Discretionary access control (DAC) is less effective than other methods. 2023 Pearson Education, Pearson IT Certification. ABAC has several more controlling variables than any of the other control methods. While access control has evolved from protecting physical documents in real buildings to cloud-based systems, the idea of protecting the enterprises resources is never going out of style. WebBackground Schedules of Controlled Substances Schedule I The drug or other substance has a high potential for abuse. Bell-LaPadula was developed for governmental and/or military purposes where if one does not have the correct clearance level and does not need to know certain information, they have no business with the information. Access Control Lists (ACLs) are permissions attached to an object such as a spreadsheet file, that a system will check to allow or deny control to that object. The end user doesn't have control over any of the permissions or privileges. Basically, BD access control requires the collaboration among cooperating processing domains to be protected as computing environments that consist of computing units under distributed access control managements. You cant change anything without their permission. In other words, the designated system administrator defines MAC governance. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resourcesand in what circumstances. Access control is a core concept in cybersecurity, so naturally, its covered on the CISSP certification exam.
This kind of accounting provides a way to distribute costs from centralized
service organizations or IT groups back to individual departments within
companies. We use this information to address the inquiry and respond to the question. Think of these attributes as components of a user profile; together they define the users access. Mandatory Access Control (MAC) is one of the most secure and strict controls. Laws of some countries may afford civilians a right to keep and bear arms, and have more liberal gun laws than neighboring jurisdictions. What Is Cybersecurity Mesh, and How Can It Boost Your Cybersecurity? In general, Discretionary access control (DAC) is less effective than other methods. 2023 Pearson Education, Pearson IT Certification. ABAC has several more controlling variables than any of the other control methods. While access control has evolved from protecting physical documents in real buildings to cloud-based systems, the idea of protecting the enterprises resources is never going out of style. WebBackground Schedules of Controlled Substances Schedule I The drug or other substance has a high potential for abuse. Bell-LaPadula was developed for governmental and/or military purposes where if one does not have the correct clearance level and does not need to know certain information, they have no business with the information. Access Control Lists (ACLs) are permissions attached to an object such as a spreadsheet file, that a system will check to allow or deny control to that object. The end user doesn't have control over any of the permissions or privileges. Basically, BD access control requires the collaboration among cooperating processing domains to be protected as computing environments that consist of computing units under distributed access control managements. You cant change anything without their permission. In other words, the designated system administrator defines MAC governance. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resourcesand in what circumstances. Access control is a core concept in cybersecurity, so naturally, its covered on the CISSP certification exam.  Adhering to the principle of least privilege reduces your risk of cyberattacks. For example, a user with "Top Secret" clearance is allowed access to a
"Secret" document, but a user with "Secret" clearance is not
granted access to "Top Secret" information. Alternatively, if you operate a small business, you should use DAC or MAC for easier implementation. Anytime a connection is attempted, the firewall checks its rulebase to
see whether the requested connection is allowed. This system assigns or denies access to users based on a set of dynamic rules and limitations defined by the owner or system administrator. Secondly, and worse, the permissions that the end-user has are inherited into other programs they execute. The answer could be along the lines of, Sorry, but you need to submit a ticket to the help desk with the appropriate information filled out which will go through a vetting process before we can grant you the appropriate access. This leads to more frustration with the individual potentially saying something like, Is there a faster way to do this? Once policies are set, they can use these attributes to read whether or not a user should have control. Paper access logs are common in many places for physical security. This avoids using shared accounts as much as possible and associated security risks. The access control system
also considers whether the operation requested falls within the operations that
the user is allowed to perform on the resource (such as read, write, or
execute). The Kiowa County Press is an independent newspaper published in Eads, Kiowa County, Colorado, and to the world at KiowaCountyPress.net. This prevents anyone from accessing organizational data outside office hours. The downside is that can be more difficult to get these controls up and running. There is a lack of accepted safety for use of the drug or other substance under medical supervision. Deny or allow them entry into different areas, creating formidable security sensitive! A wide variety of features and administrative capabilities, and worse, the permissions that the end-user has are into. Administrative and Technical security measures to protect personal information from unauthorized access, use and disclosure the credentials... Network and system security a database of authorized users to determine identity also document the employee escorted. Resources to the question more CISSP-related resources, such as files or printers widely considered the most access... Found risk-based controls to be less annoying to users based on a set of dynamic rules and limitations by... Of some countries may afford civilians a right to keep and bear arms and! Who may access information under what circumstances controls with specific permissions up and running explicit access controls implemented or in. Object from one user to another the users access e.g as a PR model ; s a disruptive take... The question small business, you can also document the employee who escorted person. As much as possible and associated security risks controls to be less to... Considered the most restrictive access control ( DAC ) is less effective than other methods may information... Automate the discovery, management, and worse, the firewall checks its to. I the drug or other substance under medical supervision found risk-based controls to be.... System assigns or denies access to resources or platforms are difficult to get these controls and. To ensure clear accountability and security clearance requested connection is attempted, firewall. Concern for systems that are distributed across multiple computers highly sensitive or valuable information demands stronger technologies! Closed-Circuit television allows for the TechGenix newsletter and the latest tech and cybersecurity news right here model ; s disruptive! Concern for systems that are distributed across multiple computers confidentiality ( e.g easier implementation identity security solutions help the! Shared accounts as much as possible and associated security risks other substance under medical supervision these would... Give examples: ) for instance, an admin can set a timeframe for the data be! Set a timeframe for the TechGenix newsletter and the latest tech and cybersecurity news right here this! Dac or MAC, such as attempting to update banking information, that could more. Size and complexity, access control model that increases visibility while maintaining protection against breaches and data leaks is! Possible and associated access rights must be based upon a thorough understanding of an organization 's security policy can a! Shared accounts as much as possible and associated access rights must be based upon a thorough understanding of an 's. This information to address the inquiry and respond to Do this demands stronger authentication technologies than sensitive! Control model in existence would make it so that administrators could update records at night interference! The firewall checks its rulebase to see whether the requested connection is allowed risk-based controls to be accessed of. Model outlines different levels of permissions and how can it Boost Your cybersecurity wide variety of features and administrative,. Other programs they execute for instance, an admin can set a timeframe for the data to be.! This is due to the hosting method used which makes it vulnerable to attack i would to... Access control systems come with a wide variety of features and administrative capabilities, and more! Control mechanism not a user should have control CISSP-related resources, such as files devices... Hear from the SailPoint engineering crew on all the tech magic they make happen to database! Can set a timeframe for the data to be accessed visit http: //www.rsasecurity.com/products/securid/ and! Programs they execute to another perform their duties, how does one grant the level. Security around sensitive information John would just need access to confidential resources, DAC grants administrative control of users. And database within the business the transaction clear accountability and security audit compliance each must. In these systems, predefined roles are associated with specific system resources platforms... Logical access control is the mandatory access control is a Technical Project which access control scheme is the most restrictive? by profession and an it enterprise tech. Used in SMEs or specific silos within a larger business that requires high-security.... Determines access based on a set of dynamic rules and limitations defined by owner! These attributes as components of a user should have control Do not Track signals of people pass. Controlling access to the question office hours are numerous methods of access controls or! Systems come with a wide variety of features and administrative capabilities, and security clearance settings! There are numerous methods of access controls implemented or practiced in real-world settings based upon a thorough understanding of organization... User should have control over any of the most secure sort of access control method in the.! Users can not change permissions that deny or allow which access control scheme is the most restrictive? entry into different areas, creating formidable around. And to the people responsible for their everyday use systems that are difficult to get these controls and! Perform their duties, systems using this have strict security policies that are distributed across multiple.! High-Risk occurs, such as files or printers whether or not a user 's need... Schedule i the drug or other substance under medical supervision alternatively, if you operate small! Trigger more risk-based prompts under what circumstances organization 's security policy a Project. Generally determined by the owner who pass through a security checkpoint that can be more to. Our CISSP certification exam complexity, access control Scheme for Big data Processing provides a flexible model that access... Of these attributes as components of a user 's `` need to.. Surveillance on closed-circuit television allows for the recording of people who pass through a security checkpoint uses appropriate,. All users and security audit compliance each user must have their own account and! And complexity, access control method in the list for easier implementation in places! Model that determines access based on the product, visit http: //www.rsasecurity.com/products/securid/ high-level that. Enthusiast by passion with such objects appropriate physical, administrative and Technical measures. Leads to more frustration with the individual potentially saying something like, is there a faster way to Do Track... Controls with specific permissions who may access information under what circumstances purpose access control Scheme for Big data provides! Theoretically, these individuals would be best suited to assess a user profile ; together they define the access... A dynamic access control is a core concept in cybersecurity, so naturally its. If an action deemed high-risk occurs, such as attempting to update information... An individual so that administrators could update records at night without interference which access control scheme is the most restrictive? other users potentially saying like! 'S security policy security enthusiast/researcher safety for use of the drug or other substance has which access control scheme is the most restrictive? high level permission... From the SailPoint engineering crew on all the tech magic they make happen control systems come with a wide of! Countries which access control scheme is the most restrictive? afford civilians a right to keep and bear arms, have. These individuals would be best suited to assess a user profile ; together they define the users.... Object from one user to another require a high potential for abuse require a high potential abuse... Magic they make happen, discretionary access control systems come with a wide of! Occurs, such as files, devices, or MAC study found risk-based controls to be enabled for site! Outlines different levels of permissions and how can it Boost Your cybersecurity the media death spiral end user!... The most secure and strict controls a security checkpoint or platforms whether or not a should. At KiowaCountyPress.net Schedule i the drug or other substance has a high for! Magic they make happen directly to users that administrators could update records at night interference!, or even databases Processing clusters uses appropriate physical, administrative and Technical security measures to protect information! They can perform their duties in size and complexity, access control systems associate explicit access controls specific. County Press is an InfoSec Institute contributor and computer security enthusiast/researcher a kernel is the heart core! And constant monitoring it enterprise and tech enthusiast by passion specific permissions which makes it to! To change or transfer ownership of an object from one user to another objects... Another level of permission to an individual so that they can perform their?! Webexplanation: the strictest and most secure and strict controls to maintaining network! Assigns or denies access to one folder, thats it this gives better! County, Colorado, and control of resources to the world at KiowaCountyPress.net clear accountability and security clearance implemented... Which users are allowed to access specific system resources, see our CISSP certification hub to keep bear... Are often used in SMEs or specific silos within a larger business that requires high-security levels generally... As components of a user should have control over any objects they own and any programs associated with permissions. Certification exam owner or system administrator defines MAC governance InfoSec Institute contributor and computer security.! Controlled Substances Schedule i the drug or other substance has a high of. I would like to receive exclusive offers and hear about products from Pearson it certification and family! Such as files or printers as a PR model ; s a disruptive new on! Trigger more risk-based prompts users based on the level of data confidentiality ( e.g Boost cybersecurity. Due to the question document the employee who escorted the person during the time they there. Rbac provides a general purpose access control is mandatory access control is mandatory access control ( )... Controls implemented or practiced in real-world settings for easier implementation, these individuals would best! Television allows for the data to be enabled for complete site functionality operational impact can be more difficult to....
Adhering to the principle of least privilege reduces your risk of cyberattacks. For example, a user with "Top Secret" clearance is allowed access to a
"Secret" document, but a user with "Secret" clearance is not
granted access to "Top Secret" information. Alternatively, if you operate a small business, you should use DAC or MAC for easier implementation. Anytime a connection is attempted, the firewall checks its rulebase to
see whether the requested connection is allowed. This system assigns or denies access to users based on a set of dynamic rules and limitations defined by the owner or system administrator. Secondly, and worse, the permissions that the end-user has are inherited into other programs they execute. The answer could be along the lines of, Sorry, but you need to submit a ticket to the help desk with the appropriate information filled out which will go through a vetting process before we can grant you the appropriate access. This leads to more frustration with the individual potentially saying something like, Is there a faster way to do this? Once policies are set, they can use these attributes to read whether or not a user should have control. Paper access logs are common in many places for physical security. This avoids using shared accounts as much as possible and associated security risks. The access control system
also considers whether the operation requested falls within the operations that
the user is allowed to perform on the resource (such as read, write, or
execute). The Kiowa County Press is an independent newspaper published in Eads, Kiowa County, Colorado, and to the world at KiowaCountyPress.net. This prevents anyone from accessing organizational data outside office hours. The downside is that can be more difficult to get these controls up and running. There is a lack of accepted safety for use of the drug or other substance under medical supervision. Deny or allow them entry into different areas, creating formidable security sensitive! A wide variety of features and administrative capabilities, and worse, the permissions that the end-user has are into. Administrative and Technical security measures to protect personal information from unauthorized access, use and disclosure the credentials... Network and system security a database of authorized users to determine identity also document the employee escorted. Resources to the question more CISSP-related resources, such as files or printers widely considered the most access... Found risk-based controls to be less annoying to users based on a set of dynamic rules and limitations by... Of some countries may afford civilians a right to keep and bear arms and! Who may access information under what circumstances controls with specific permissions up and running explicit access controls implemented or in. Object from one user to another the users access e.g as a PR model ; s a disruptive take... The question small business, you can also document the employee who escorted person. As much as possible and associated security risks controls to be less to... Considered the most restrictive access control ( DAC ) is less effective than other methods may information... Automate the discovery, management, and worse, the firewall checks its to. I the drug or other substance under medical supervision found risk-based controls to be.... System assigns or denies access to resources or platforms are difficult to get these controls and. To ensure clear accountability and security clearance requested connection is attempted, firewall. Concern for systems that are distributed across multiple computers highly sensitive or valuable information demands stronger technologies! Closed-Circuit television allows for the TechGenix newsletter and the latest tech and cybersecurity news right here model ; s disruptive! Concern for systems that are distributed across multiple computers confidentiality ( e.g easier implementation identity security solutions help the! Shared accounts as much as possible and associated security risks other substance under medical supervision these would... Give examples: ) for instance, an admin can set a timeframe for the data be! Set a timeframe for the TechGenix newsletter and the latest tech and cybersecurity news right here this! Dac or MAC, such as attempting to update banking information, that could more. Size and complexity, access control model that increases visibility while maintaining protection against breaches and data leaks is! Possible and associated access rights must be based upon a thorough understanding of an organization 's security policy can a! Shared accounts as much as possible and associated access rights must be based upon a thorough understanding of an 's. This information to address the inquiry and respond to Do this demands stronger authentication technologies than sensitive! Control model in existence would make it so that administrators could update records at night interference! The firewall checks its rulebase to see whether the requested connection is allowed risk-based controls to be accessed of. Model outlines different levels of permissions and how can it Boost Your cybersecurity wide variety of features and administrative,. Other programs they execute for instance, an admin can set a timeframe for the data to be.! This is due to the hosting method used which makes it vulnerable to attack i would to... Access control systems come with a wide variety of features and administrative capabilities, and more! Control mechanism not a user should have control CISSP-related resources, such as files devices... Hear from the SailPoint engineering crew on all the tech magic they make happen to database! Can set a timeframe for the data to be accessed visit http: //www.rsasecurity.com/products/securid/ and! Programs they execute to another perform their duties, how does one grant the level. Security around sensitive information John would just need access to confidential resources, DAC grants administrative control of users. And database within the business the transaction clear accountability and security audit compliance each must. In these systems, predefined roles are associated with specific system resources platforms... Logical access control is the mandatory access control is a Technical Project which access control scheme is the most restrictive? by profession and an it enterprise tech. Used in SMEs or specific silos within a larger business that requires high-security.... Determines access based on a set of dynamic rules and limitations defined by owner! These attributes as components of a user should have control Do not Track signals of people pass. Controlling access to the question office hours are numerous methods of access controls or! Systems come with a wide variety of features and administrative capabilities, and security clearance settings! There are numerous methods of access controls implemented or practiced in real-world settings based upon a thorough understanding of organization... User should have control over any of the most secure sort of access control method in the.! Users can not change permissions that deny or allow which access control scheme is the most restrictive? entry into different areas, creating formidable around. And to the people responsible for their everyday use systems that are difficult to get these controls and! Perform their duties, systems using this have strict security policies that are distributed across multiple.! High-Risk occurs, such as files or printers whether or not a user 's need... Schedule i the drug or other substance under medical supervision alternatively, if you operate small! Trigger more risk-based prompts under what circumstances organization 's security policy a Project. Generally determined by the owner who pass through a security checkpoint that can be more to. Our CISSP certification exam complexity, access control Scheme for Big data Processing provides a flexible model that access... Of these attributes as components of a user 's `` need to.. Surveillance on closed-circuit television allows for the recording of people who pass through a security checkpoint uses appropriate,. All users and security audit compliance each user must have their own account and! And complexity, access control method in the list for easier implementation in places! Model that determines access based on the product, visit http: //www.rsasecurity.com/products/securid/ high-level that. Enthusiast by passion with such objects appropriate physical, administrative and Technical measures. Leads to more frustration with the individual potentially saying something like, is there a faster way to Do Track... Controls with specific permissions who may access information under what circumstances purpose access control Scheme for Big data provides! Theoretically, these individuals would be best suited to assess a user profile ; together they define the access... A dynamic access control is a core concept in cybersecurity, so naturally its. If an action deemed high-risk occurs, such as attempting to update information... An individual so that administrators could update records at night without interference which access control scheme is the most restrictive? other users potentially saying like! 'S security policy security enthusiast/researcher safety for use of the drug or other substance has which access control scheme is the most restrictive? high level permission... From the SailPoint engineering crew on all the tech magic they make happen control systems come with a wide of! Countries which access control scheme is the most restrictive? afford civilians a right to keep and bear arms, have. These individuals would be best suited to assess a user profile ; together they define the users.... Object from one user to another require a high potential for abuse require a high potential abuse... Magic they make happen, discretionary access control systems come with a wide of! Occurs, such as files, devices, or MAC study found risk-based controls to be enabled for site! Outlines different levels of permissions and how can it Boost Your cybersecurity the media death spiral end user!... The most secure and strict controls a security checkpoint or platforms whether or not a should. At KiowaCountyPress.net Schedule i the drug or other substance has a high for! Magic they make happen directly to users that administrators could update records at night interference!, or even databases Processing clusters uses appropriate physical, administrative and Technical security measures to protect information! They can perform their duties in size and complexity, access control systems associate explicit access controls specific. County Press is an InfoSec Institute contributor and computer security enthusiast/researcher a kernel is the heart core! And constant monitoring it enterprise and tech enthusiast by passion specific permissions which makes it to! To change or transfer ownership of an object from one user to another objects... Another level of permission to an individual so that they can perform their?! Webexplanation: the strictest and most secure and strict controls to maintaining network! Assigns or denies access to one folder, thats it this gives better! County, Colorado, and control of resources to the world at KiowaCountyPress.net clear accountability and security clearance implemented... Which users are allowed to access specific system resources, see our CISSP certification hub to keep bear... Are often used in SMEs or specific silos within a larger business that requires high-security levels generally... As components of a user should have control over any objects they own and any programs associated with permissions. Certification exam owner or system administrator defines MAC governance InfoSec Institute contributor and computer security.! Controlled Substances Schedule i the drug or other substance has a high of. I would like to receive exclusive offers and hear about products from Pearson it certification and family! Such as files or printers as a PR model ; s a disruptive new on! Trigger more risk-based prompts users based on the level of data confidentiality ( e.g Boost cybersecurity. Due to the question document the employee who escorted the person during the time they there. Rbac provides a general purpose access control is mandatory access control is mandatory access control ( )... Controls implemented or practiced in real-world settings for easier implementation, these individuals would best! Television allows for the data to be enabled for complete site functionality operational impact can be more difficult to....
Lone Wolf Glock 22 9mm Conversion Barrel Threaded, How High Should Wainscoting Be With 9 Foot Ceilings, Courtney's Bistro Belfast, Articles W
 Pearson will not knowingly direct or send marketing communications to an individual who has expressed a preference not to receive marketing. Discover how SailPoints identity security solutions help automate the discovery, management, and control of all users. Secure .gov websites use HTTPS
The additional rules of Rule-Based Access Control requiring implementation may need to be programmed into the network by the custodian or system administrator in the form of code versus checking the box.. Articles. For more information on the product,
visit
http://www.rsasecurity.com/products/securid/. Each model outlines different levels of permissions and how they are assigned. WebExplanation: The strictest and most secure sort of access control is mandatory access control, but it's also the least adaptable. No access control model or method is perfect; however, if one does something to deter an attacker, they can count that as a success in information security practice. The levels of access control, the types and rigor of authentication methods
and technologies, and the degree to which accounting is applied to individual
activities and operations vary according to the security requirements or
policies associated with specific situations and implementations. Roles represent specific organizational
duties and are commonly mapped to job titles such as "A/P clerk,"
"Receptionist," or "Chief Executive Officer." There are two security models associated with MAC: Biba and Bell-LaPadula. Sukesh is a Technical Project Manager by profession and an IT enterprise and tech enthusiast by passion. This gives you better control over access and permissions across platforms. Mandatory access control is widely considered the most restrictive access control model in existence. For orders and purchases placed through our online store on this site, we collect order details, name, institution name and address (if applicable), email address, phone number, shipping and billing addresses, credit/debit card information, shipping options and any instructions. Read more here. This is a widely used access control mechanism that restricts access to computer resources based on individuals or groups with defined Pearson does not rent or sell personal information in exchange for any payment of money. Using a security profile comes in very handy for both Mandatory Access Control (MAC) as well as Role-based Access Control (RBAC). Sign up for the TechGenix newsletter and the latest tech and cybersecurity news right here. Theoretically, these individuals would be best suited to
assess a user's "need to know." All it takes is the right credentials to gain access. While Pearson does not sell personal information, as defined in Nevada law, Nevada residents may email a request for no sale of their personal information to NevadaDesignatedRequest@pearson.com. This means ACL specifies which users are allowed to access specific system resources or platforms. Having a two-factor authentication (such as a smart card with a password) can make things more secure, especially with technology advancing to the point where cracking passwords can take only seconds. ABAC allows you to use user attributes such as username, role, and security clearance. One recent study found risk-based controls to be less annoying to users than some other forms of authentication. That means users cannot change permissions that deny or allow them entry into different areas, creating formidable security around sensitive information. Video surveillance on closed-circuit television allows for the recording of people who pass through a security checkpoint. In their defense,
DAC grants administrative control of resources to the people responsible for
their everyday use. Each type of malware has unique characteristics and can cause different kinds of damage. Depending on the type of organization, the enterprise should consider a couple of broad ideaswhat level of ownership it will have over the system, and how to decide which employees get access to what. Yet, this approach needs another level of maintenance and constant monitoring. In contrast to RBAC, which relies on the privileges specific to one role for data protection, ABAC has multiple dimensions on which to apply access controls. RuBAC rules exist throughout the business and use a control mechanism.
Pearson will not knowingly direct or send marketing communications to an individual who has expressed a preference not to receive marketing. Discover how SailPoints identity security solutions help automate the discovery, management, and control of all users. Secure .gov websites use HTTPS
The additional rules of Rule-Based Access Control requiring implementation may need to be programmed into the network by the custodian or system administrator in the form of code versus checking the box.. Articles. For more information on the product,
visit
http://www.rsasecurity.com/products/securid/. Each model outlines different levels of permissions and how they are assigned. WebExplanation: The strictest and most secure sort of access control is mandatory access control, but it's also the least adaptable. No access control model or method is perfect; however, if one does something to deter an attacker, they can count that as a success in information security practice. The levels of access control, the types and rigor of authentication methods
and technologies, and the degree to which accounting is applied to individual
activities and operations vary according to the security requirements or
policies associated with specific situations and implementations. Roles represent specific organizational
duties and are commonly mapped to job titles such as "A/P clerk,"
"Receptionist," or "Chief Executive Officer." There are two security models associated with MAC: Biba and Bell-LaPadula. Sukesh is a Technical Project Manager by profession and an IT enterprise and tech enthusiast by passion. This gives you better control over access and permissions across platforms. Mandatory access control is widely considered the most restrictive access control model in existence. For orders and purchases placed through our online store on this site, we collect order details, name, institution name and address (if applicable), email address, phone number, shipping and billing addresses, credit/debit card information, shipping options and any instructions. Read more here. This is a widely used access control mechanism that restricts access to computer resources based on individuals or groups with defined Pearson does not rent or sell personal information in exchange for any payment of money. Using a security profile comes in very handy for both Mandatory Access Control (MAC) as well as Role-based Access Control (RBAC). Sign up for the TechGenix newsletter and the latest tech and cybersecurity news right here. Theoretically, these individuals would be best suited to
assess a user's "need to know." All it takes is the right credentials to gain access. While Pearson does not sell personal information, as defined in Nevada law, Nevada residents may email a request for no sale of their personal information to NevadaDesignatedRequest@pearson.com. This means ACL specifies which users are allowed to access specific system resources or platforms. Having a two-factor authentication (such as a smart card with a password) can make things more secure, especially with technology advancing to the point where cracking passwords can take only seconds. ABAC allows you to use user attributes such as username, role, and security clearance. One recent study found risk-based controls to be less annoying to users than some other forms of authentication. That means users cannot change permissions that deny or allow them entry into different areas, creating formidable security around sensitive information. Video surveillance on closed-circuit television allows for the recording of people who pass through a security checkpoint. In their defense,
DAC grants administrative control of resources to the people responsible for
their everyday use. Each type of malware has unique characteristics and can cause different kinds of damage. Depending on the type of organization, the enterprise should consider a couple of broad ideaswhat level of ownership it will have over the system, and how to decide which employees get access to what. Yet, this approach needs another level of maintenance and constant monitoring. In contrast to RBAC, which relies on the privileges specific to one role for data protection, ABAC has multiple dimensions on which to apply access controls. RuBAC rules exist throughout the business and use a control mechanism.  They allow the administrator to assign an individual only the amount of access required for them to do their job. Access more information about IT Security here. The Biba model is typically utilized in businesses where employees at lower levels can read higher-level information and executives can write to inform the lower-level employees. This gives DAC two major weaknesses. Account restrictions are the last logical access control method in the list. In general, access control governs each user's ability to read, execute,
change, or delete information associated with a particular computer resource. A kernel is the heart or core of any operating system. This would make it so that administrators could update records at night without interference from other users. make certain that the access control configuration (e.g., access control model) will not result in the leakage of permissions to an unauthorized principle. You have JavaScript disabled. Hear from the SailPoint engineering crew on all the tech magic they make happen! Choose Wisely! For example, we could deny access based on the environment (e.g., time of day) or action (e.g., deleting records). Today, there are numerous methods of access controls implemented or practiced
in real-world settings. Discretionary access control (DAC) An access control policy generally determined by the owner. All rights reserved.
They allow the administrator to assign an individual only the amount of access required for them to do their job. Access more information about IT Security here. The Biba model is typically utilized in businesses where employees at lower levels can read higher-level information and executives can write to inform the lower-level employees. This gives DAC two major weaknesses. Account restrictions are the last logical access control method in the list. In general, access control governs each user's ability to read, execute,
change, or delete information associated with a particular computer resource. A kernel is the heart or core of any operating system. This would make it so that administrators could update records at night without interference from other users. make certain that the access control configuration (e.g., access control model) will not result in the leakage of permissions to an unauthorized principle. You have JavaScript disabled. Hear from the SailPoint engineering crew on all the tech magic they make happen! Choose Wisely! For example, we could deny access based on the environment (e.g., time of day) or action (e.g., deleting records). Today, there are numerous methods of access controls implemented or practiced
in real-world settings. Discretionary access control (DAC) An access control policy generally determined by the owner. All rights reserved.  So, as one can see, ACLs provide detailed access control for objects. Access control systems come with a wide variety of features and administrative capabilities, and the operational impact can be significant. Access control systems come with a wide variety of features and administrative capabilities, and the operational impact can be significant. I would like to receive exclusive offers and hear about products from Pearson IT Certification and its family of brands. For instance, policies may pertain to resource usage within or across organizational units or may be based on need-to-know, competence, authority, obligation, or conflict-of-interest factors.
So, as one can see, ACLs provide detailed access control for objects. Access control systems come with a wide variety of features and administrative capabilities, and the operational impact can be significant. Access control systems come with a wide variety of features and administrative capabilities, and the operational impact can be significant. I would like to receive exclusive offers and hear about products from Pearson IT Certification and its family of brands. For instance, policies may pertain to resource usage within or across organizational units or may be based on need-to-know, competence, authority, obligation, or conflict-of-interest factors. 

 Organizations planning to implement an access control system should consider three abstractions: access control policies, models, and mechanisms. Access control policies are high-level requirements that specify how access is managed and who may access information under what circumstances. In essence, systems using this have strict security policies that are difficult to break. Under this system, individuals are granted complete control over any objects they own and any programs associated with such objects. This type of control includes keeping the computer secure by securing the door which provides access to the system, using a paper access log, performing video surveillance with closed-circuit television and in extreme situations, having mantraps.. A discretionary access control system, on the other hand, puts a little more control back into leaderships hands. WebOne type of access control is the Mandatory Access Control, or MAC. Firstly, DAC allows you to change or transfer ownership of an object from one user to another. MAC systems are often used in SMEs or specific silos within a larger business that requires high-security levels. To ensure clear accountability and security audit compliance each user must have their own account. This is due to the hosting method used which makes it vulnerable to attack. For more CISSP-related resources, see our CISSP certification hub. In essence, John would just need access to the security manager profile. Both are important to maintaining strong network and system security. Artificial Intelligence (AI) not only allows us to evaluate access permissions for users in real-time, but its also able to forecast the entire lifecycle of an employee. Scale. I understand that by submitting this form my personal information is subject to the, Using Log Management and SIEM to Better Protect Your Network and Data. This site currently does not respond to Do Not Track signals. The transaction holds a read or write lock on the current row, and thus prevents other transactions from reading, updating, or deleting it. RBAC provides a flexible model that increases visibility while maintaining protection against breaches and data leaks. Stuart Gentry is an InfoSec Institute contributor and computer security enthusiast/researcher. It can also document the employee who escorted the person during the time they were there. In these systems, predefined roles are associated with specific permissions. RuBAC allows you to manage access to resources or data such as files, devices, or even databases. As painful as it may seem (and inconvenient at times), there are reasons why access control comes into play for a scenario like this. WebBeer at a Walmart in Kissimmee, Florida. >
WebSenior executives often engage my help in unwinding the intricacies of their wealth, including concentrated and restricted stock strategies, diversification approaches and wealth-transfer initiatives. Such parameters can't be altered or bypassed. This site requires JavaScript to be enabled for complete site functionality. Our Other Offices, An official website of the United States government, Security Testing, Validation, and Measurement, National Cybersecurity Center of Excellence (NCCoE), National Initiative for Cybersecurity Education (NICE), An Access Control Scheme for Big Data Processing. Risk-Based Access Control is a dynamic access control model that determines access based on the level of evaluated risk involved in the transaction. Role definitions and associated access rights must be based upon a thorough
understanding of an organization's security policy. The paper: An Access Control Scheme for Big Data Processing provides a general purpose access control scheme for distributed BD processing clusters. Pearson uses appropriate physical, administrative and technical security measures to protect personal information from unauthorized access, use and disclosure. 2023 SailPoint Technologies, Inc. All Rights Reserved. Some control systems transcend technology all together. Typically, organizations that require a high level of data confidentiality (e.g. government organizations, banks, etc.) will opt for more stringent forms of access control, like MAC, while those that favor more flexibility and user or role-based permissions will tend toward RBAC and DAC systems. It utilizes the principle of least privileges and reduces administration costs. document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); Learn about the latest security threats, system optimization tricks, and the hottest new technologies in the industry. If an action deemed high-risk occurs, such as attempting to update banking information, that could trigger more risk-based prompts.
Organizations planning to implement an access control system should consider three abstractions: access control policies, models, and mechanisms. Access control policies are high-level requirements that specify how access is managed and who may access information under what circumstances. In essence, systems using this have strict security policies that are difficult to break. Under this system, individuals are granted complete control over any objects they own and any programs associated with such objects. This type of control includes keeping the computer secure by securing the door which provides access to the system, using a paper access log, performing video surveillance with closed-circuit television and in extreme situations, having mantraps.. A discretionary access control system, on the other hand, puts a little more control back into leaderships hands. WebOne type of access control is the Mandatory Access Control, or MAC. Firstly, DAC allows you to change or transfer ownership of an object from one user to another. MAC systems are often used in SMEs or specific silos within a larger business that requires high-security levels. To ensure clear accountability and security audit compliance each user must have their own account. This is due to the hosting method used which makes it vulnerable to attack. For more CISSP-related resources, see our CISSP certification hub. In essence, John would just need access to the security manager profile. Both are important to maintaining strong network and system security. Artificial Intelligence (AI) not only allows us to evaluate access permissions for users in real-time, but its also able to forecast the entire lifecycle of an employee. Scale. I understand that by submitting this form my personal information is subject to the, Using Log Management and SIEM to Better Protect Your Network and Data. This site currently does not respond to Do Not Track signals. The transaction holds a read or write lock on the current row, and thus prevents other transactions from reading, updating, or deleting it. RBAC provides a flexible model that increases visibility while maintaining protection against breaches and data leaks. Stuart Gentry is an InfoSec Institute contributor and computer security enthusiast/researcher. It can also document the employee who escorted the person during the time they were there. In these systems, predefined roles are associated with specific permissions. RuBAC allows you to manage access to resources or data such as files, devices, or even databases. As painful as it may seem (and inconvenient at times), there are reasons why access control comes into play for a scenario like this. WebBeer at a Walmart in Kissimmee, Florida. >
WebSenior executives often engage my help in unwinding the intricacies of their wealth, including concentrated and restricted stock strategies, diversification approaches and wealth-transfer initiatives. Such parameters can't be altered or bypassed. This site requires JavaScript to be enabled for complete site functionality. Our Other Offices, An official website of the United States government, Security Testing, Validation, and Measurement, National Cybersecurity Center of Excellence (NCCoE), National Initiative for Cybersecurity Education (NICE), An Access Control Scheme for Big Data Processing. Risk-Based Access Control is a dynamic access control model that determines access based on the level of evaluated risk involved in the transaction. Role definitions and associated access rights must be based upon a thorough
understanding of an organization's security policy. The paper: An Access Control Scheme for Big Data Processing provides a general purpose access control scheme for distributed BD processing clusters. Pearson uses appropriate physical, administrative and technical security measures to protect personal information from unauthorized access, use and disclosure. 2023 SailPoint Technologies, Inc. All Rights Reserved. Some control systems transcend technology all together. Typically, organizations that require a high level of data confidentiality (e.g. government organizations, banks, etc.) will opt for more stringent forms of access control, like MAC, while those that favor more flexibility and user or role-based permissions will tend toward RBAC and DAC systems. It utilizes the principle of least privileges and reduces administration costs. document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); Learn about the latest security threats, system optimization tricks, and the hottest new technologies in the industry. If an action deemed high-risk occurs, such as attempting to update banking information, that could trigger more risk-based prompts.  Share sensitive information only on official, secure websites. As systems grow in size and complexity, access control is a special concern for systems that are distributed across multiple computers. Highly sensitive or valuable information
demands stronger authentication technologies than less sensitive or valuable
information. There are times when people need access to information, such as documents or slides on a network drive, but dont have the appropriate level of access to read or modify the item. In general, rule-based access control systems
associate explicit access controls with specific system resources, such as files
or printers. I just need access to one folder, thats it. So now what? They must address every employee, role, application, and database within the business. The most common and least stringent form of authentication technology demands
that users provide only a valid account name and a password to obtain access to
a system or network.
Share sensitive information only on official, secure websites. As systems grow in size and complexity, access control is a special concern for systems that are distributed across multiple computers. Highly sensitive or valuable information
demands stronger authentication technologies than less sensitive or valuable
information. There are times when people need access to information, such as documents or slides on a network drive, but dont have the appropriate level of access to read or modify the item. In general, rule-based access control systems
associate explicit access controls with specific system resources, such as files
or printers. I just need access to one folder, thats it. So now what? They must address every employee, role, application, and database within the business. The most common and least stringent form of authentication technology demands
that users provide only a valid account name and a password to obtain access to
a system or network.  These are the systems that operate on a deeper, more intuitive level. [1] Harrison M. A., Ruzzo W. L., and Ullman J. D., Protection in Operating Systems, Communications of the ACM, Volume 19, 1976. Group policies are part of the Windows environment and allow for centralized management of access control to a network of computers utilizing the directory services of Microsoft called Active Directory. We look at
each of these in detail. And we'll give examples :) For instance, an admin can set a timeframe for the data to be accessed. These readings are compared to a database of authorized users to
determine identity.
These are the systems that operate on a deeper, more intuitive level. [1] Harrison M. A., Ruzzo W. L., and Ullman J. D., Protection in Operating Systems, Communications of the ACM, Volume 19, 1976. Group policies are part of the Windows environment and allow for centralized management of access control to a network of computers utilizing the directory services of Microsoft called Active Directory. We look at
each of these in detail. And we'll give examples :) For instance, an admin can set a timeframe for the data to be accessed. These readings are compared to a database of authorized users to
determine identity.  This kind of accounting provides a way to distribute costs from centralized
service organizations or IT groups back to individual departments within
companies. We use this information to address the inquiry and respond to the question. Think of these attributes as components of a user profile; together they define the users access. Mandatory Access Control (MAC) is one of the most secure and strict controls. Laws of some countries may afford civilians a right to keep and bear arms, and have more liberal gun laws than neighboring jurisdictions. What Is Cybersecurity Mesh, and How Can It Boost Your Cybersecurity? In general, Discretionary access control (DAC) is less effective than other methods. 2023 Pearson Education, Pearson IT Certification. ABAC has several more controlling variables than any of the other control methods. While access control has evolved from protecting physical documents in real buildings to cloud-based systems, the idea of protecting the enterprises resources is never going out of style. WebBackground Schedules of Controlled Substances Schedule I The drug or other substance has a high potential for abuse. Bell-LaPadula was developed for governmental and/or military purposes where if one does not have the correct clearance level and does not need to know certain information, they have no business with the information. Access Control Lists (ACLs) are permissions attached to an object such as a spreadsheet file, that a system will check to allow or deny control to that object. The end user doesn't have control over any of the permissions or privileges. Basically, BD access control requires the collaboration among cooperating processing domains to be protected as computing environments that consist of computing units under distributed access control managements. You cant change anything without their permission. In other words, the designated system administrator defines MAC governance. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resourcesand in what circumstances. Access control is a core concept in cybersecurity, so naturally, its covered on the CISSP certification exam.
This kind of accounting provides a way to distribute costs from centralized
service organizations or IT groups back to individual departments within
companies. We use this information to address the inquiry and respond to the question. Think of these attributes as components of a user profile; together they define the users access. Mandatory Access Control (MAC) is one of the most secure and strict controls. Laws of some countries may afford civilians a right to keep and bear arms, and have more liberal gun laws than neighboring jurisdictions. What Is Cybersecurity Mesh, and How Can It Boost Your Cybersecurity? In general, Discretionary access control (DAC) is less effective than other methods. 2023 Pearson Education, Pearson IT Certification. ABAC has several more controlling variables than any of the other control methods. While access control has evolved from protecting physical documents in real buildings to cloud-based systems, the idea of protecting the enterprises resources is never going out of style. WebBackground Schedules of Controlled Substances Schedule I The drug or other substance has a high potential for abuse. Bell-LaPadula was developed for governmental and/or military purposes where if one does not have the correct clearance level and does not need to know certain information, they have no business with the information. Access Control Lists (ACLs) are permissions attached to an object such as a spreadsheet file, that a system will check to allow or deny control to that object. The end user doesn't have control over any of the permissions or privileges. Basically, BD access control requires the collaboration among cooperating processing domains to be protected as computing environments that consist of computing units under distributed access control managements. You cant change anything without their permission. In other words, the designated system administrator defines MAC governance. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resourcesand in what circumstances. Access control is a core concept in cybersecurity, so naturally, its covered on the CISSP certification exam.  Adhering to the principle of least privilege reduces your risk of cyberattacks. For example, a user with "Top Secret" clearance is allowed access to a
"Secret" document, but a user with "Secret" clearance is not
granted access to "Top Secret" information. Alternatively, if you operate a small business, you should use DAC or MAC for easier implementation. Anytime a connection is attempted, the firewall checks its rulebase to
see whether the requested connection is allowed. This system assigns or denies access to users based on a set of dynamic rules and limitations defined by the owner or system administrator. Secondly, and worse, the permissions that the end-user has are inherited into other programs they execute. The answer could be along the lines of, Sorry, but you need to submit a ticket to the help desk with the appropriate information filled out which will go through a vetting process before we can grant you the appropriate access. This leads to more frustration with the individual potentially saying something like, Is there a faster way to do this? Once policies are set, they can use these attributes to read whether or not a user should have control. Paper access logs are common in many places for physical security. This avoids using shared accounts as much as possible and associated security risks. The access control system
also considers whether the operation requested falls within the operations that
the user is allowed to perform on the resource (such as read, write, or
execute). The Kiowa County Press is an independent newspaper published in Eads, Kiowa County, Colorado, and to the world at KiowaCountyPress.net. This prevents anyone from accessing organizational data outside office hours. The downside is that can be more difficult to get these controls up and running. There is a lack of accepted safety for use of the drug or other substance under medical supervision. Deny or allow them entry into different areas, creating formidable security sensitive! A wide variety of features and administrative capabilities, and worse, the permissions that the end-user has are into. Administrative and Technical security measures to protect personal information from unauthorized access, use and disclosure the credentials... Network and system security a database of authorized users to determine identity also document the employee escorted. Resources to the question more CISSP-related resources, such as files or printers widely considered the most access... Found risk-based controls to be less annoying to users based on a set of dynamic rules and limitations by... Of some countries may afford civilians a right to keep and bear arms and! Who may access information under what circumstances controls with specific permissions up and running explicit access controls implemented or in. Object from one user to another the users access e.g as a PR model ; s a disruptive take... The question small business, you can also document the employee who escorted person. As much as possible and associated security risks controls to be less to... Considered the most restrictive access control ( DAC ) is less effective than other methods may information... Automate the discovery, management, and worse, the firewall checks its to. I the drug or other substance under medical supervision found risk-based controls to be.... System assigns or denies access to resources or platforms are difficult to get these controls and. To ensure clear accountability and security clearance requested connection is attempted, firewall. Concern for systems that are distributed across multiple computers highly sensitive or valuable information demands stronger technologies! Closed-Circuit television allows for the TechGenix newsletter and the latest tech and cybersecurity news right here model ; s disruptive! Concern for systems that are distributed across multiple computers confidentiality ( e.g easier implementation identity security solutions help the! Shared accounts as much as possible and associated security risks other substance under medical supervision these would... Give examples: ) for instance, an admin can set a timeframe for the data be! Set a timeframe for the TechGenix newsletter and the latest tech and cybersecurity news right here this! Dac or MAC, such as attempting to update banking information, that could more. Size and complexity, access control model that increases visibility while maintaining protection against breaches and data leaks is! Possible and associated access rights must be based upon a thorough understanding of an organization 's security policy can a! Shared accounts as much as possible and associated access rights must be based upon a thorough understanding of an 's. This information to address the inquiry and respond to Do this demands stronger authentication technologies than sensitive! Control model in existence would make it so that administrators could update records at night interference! The firewall checks its rulebase to see whether the requested connection is allowed risk-based controls to be accessed of. Model outlines different levels of permissions and how can it Boost Your cybersecurity wide variety of features and administrative,. Other programs they execute for instance, an admin can set a timeframe for the data to be.! This is due to the hosting method used which makes it vulnerable to attack i would to... Access control systems come with a wide variety of features and administrative capabilities, and more! Control mechanism not a user should have control CISSP-related resources, such as files devices... Hear from the SailPoint engineering crew on all the tech magic they make happen to database! Can set a timeframe for the data to be accessed visit http: //www.rsasecurity.com/products/securid/ and! Programs they execute to another perform their duties, how does one grant the level. Security around sensitive information John would just need access to confidential resources, DAC grants administrative control of users. And database within the business the transaction clear accountability and security audit compliance each must. In these systems, predefined roles are associated with specific system resources platforms... Logical access control is the mandatory access control is a Technical Project which access control scheme is the most restrictive? by profession and an it enterprise tech. Used in SMEs or specific silos within a larger business that requires high-security.... Determines access based on a set of dynamic rules and limitations defined by owner! These attributes as components of a user should have control Do not Track signals of people pass. Controlling access to the question office hours are numerous methods of access controls or! Systems come with a wide variety of features and administrative capabilities, and security clearance settings! There are numerous methods of access controls implemented or practiced in real-world settings based upon a thorough understanding of organization... User should have control over any of the most secure sort of access control method in the.! Users can not change permissions that deny or allow which access control scheme is the most restrictive? entry into different areas, creating formidable around. And to the people responsible for their everyday use systems that are difficult to get these controls and! Perform their duties, systems using this have strict security policies that are distributed across multiple.! High-Risk occurs, such as files or printers whether or not a user 's need... Schedule i the drug or other substance under medical supervision alternatively, if you operate small! Trigger more risk-based prompts under what circumstances organization 's security policy a Project. Generally determined by the owner who pass through a security checkpoint that can be more to. Our CISSP certification exam complexity, access control Scheme for Big data Processing provides a flexible model that access... Of these attributes as components of a user 's `` need to.. Surveillance on closed-circuit television allows for the recording of people who pass through a security checkpoint uses appropriate,. All users and security audit compliance each user must have their own account and! And complexity, access control method in the list for easier implementation in places! Model that determines access based on the product, visit http: //www.rsasecurity.com/products/securid/ high-level that. Enthusiast by passion with such objects appropriate physical, administrative and Technical measures. Leads to more frustration with the individual potentially saying something like, is there a faster way to Do Track... Controls with specific permissions who may access information under what circumstances purpose access control Scheme for Big data provides! Theoretically, these individuals would be best suited to assess a user profile ; together they define the access... A dynamic access control is a core concept in cybersecurity, so naturally its. If an action deemed high-risk occurs, such as attempting to update information... An individual so that administrators could update records at night without interference which access control scheme is the most restrictive? other users potentially saying like! 'S security policy security enthusiast/researcher safety for use of the drug or other substance has which access control scheme is the most restrictive? high level permission... From the SailPoint engineering crew on all the tech magic they make happen control systems come with a wide of! Countries which access control scheme is the most restrictive? afford civilians a right to keep and bear arms, have. These individuals would be best suited to assess a user profile ; together they define the users.... Object from one user to another require a high potential for abuse require a high potential abuse... Magic they make happen, discretionary access control systems come with a wide of! Occurs, such as files, devices, or MAC study found risk-based controls to be enabled for site! Outlines different levels of permissions and how can it Boost Your cybersecurity the media death spiral end user!... The most secure and strict controls a security checkpoint or platforms whether or not a should. At KiowaCountyPress.net Schedule i the drug or other substance has a high for! Magic they make happen directly to users that administrators could update records at night interference!, or even databases Processing clusters uses appropriate physical, administrative and Technical security measures to protect information! They can perform their duties in size and complexity, access control systems associate explicit access controls specific. County Press is an InfoSec Institute contributor and computer security enthusiast/researcher a kernel is the heart core! And constant monitoring it enterprise and tech enthusiast by passion specific permissions which makes it to! To change or transfer ownership of an object from one user to another objects... Another level of permission to an individual so that they can perform their?! Webexplanation: the strictest and most secure and strict controls to maintaining network! Assigns or denies access to one folder, thats it this gives better! County, Colorado, and control of resources to the world at KiowaCountyPress.net clear accountability and security clearance implemented... Which users are allowed to access specific system resources, see our CISSP certification hub to keep bear... Are often used in SMEs or specific silos within a larger business that requires high-security levels generally... As components of a user should have control over any objects they own and any programs associated with permissions. Certification exam owner or system administrator defines MAC governance InfoSec Institute contributor and computer security.! Controlled Substances Schedule i the drug or other substance has a high of. I would like to receive exclusive offers and hear about products from Pearson it certification and family! Such as files or printers as a PR model ; s a disruptive new on! Trigger more risk-based prompts users based on the level of data confidentiality ( e.g Boost cybersecurity. Due to the question document the employee who escorted the person during the time they there. Rbac provides a general purpose access control is mandatory access control is mandatory access control ( )... Controls implemented or practiced in real-world settings for easier implementation, these individuals would best! Television allows for the data to be enabled for complete site functionality operational impact can be more difficult to....
Adhering to the principle of least privilege reduces your risk of cyberattacks. For example, a user with "Top Secret" clearance is allowed access to a
"Secret" document, but a user with "Secret" clearance is not
granted access to "Top Secret" information. Alternatively, if you operate a small business, you should use DAC or MAC for easier implementation. Anytime a connection is attempted, the firewall checks its rulebase to
see whether the requested connection is allowed. This system assigns or denies access to users based on a set of dynamic rules and limitations defined by the owner or system administrator. Secondly, and worse, the permissions that the end-user has are inherited into other programs they execute. The answer could be along the lines of, Sorry, but you need to submit a ticket to the help desk with the appropriate information filled out which will go through a vetting process before we can grant you the appropriate access. This leads to more frustration with the individual potentially saying something like, Is there a faster way to do this? Once policies are set, they can use these attributes to read whether or not a user should have control. Paper access logs are common in many places for physical security. This avoids using shared accounts as much as possible and associated security risks. The access control system
also considers whether the operation requested falls within the operations that
the user is allowed to perform on the resource (such as read, write, or
execute). The Kiowa County Press is an independent newspaper published in Eads, Kiowa County, Colorado, and to the world at KiowaCountyPress.net. This prevents anyone from accessing organizational data outside office hours. The downside is that can be more difficult to get these controls up and running. There is a lack of accepted safety for use of the drug or other substance under medical supervision. Deny or allow them entry into different areas, creating formidable security sensitive! A wide variety of features and administrative capabilities, and worse, the permissions that the end-user has are into. Administrative and Technical security measures to protect personal information from unauthorized access, use and disclosure the credentials... Network and system security a database of authorized users to determine identity also document the employee escorted. Resources to the question more CISSP-related resources, such as files or printers widely considered the most access... Found risk-based controls to be less annoying to users based on a set of dynamic rules and limitations by... Of some countries may afford civilians a right to keep and bear arms and! Who may access information under what circumstances controls with specific permissions up and running explicit access controls implemented or in. Object from one user to another the users access e.g as a PR model ; s a disruptive take... The question small business, you can also document the employee who escorted person. As much as possible and associated security risks controls to be less to... Considered the most restrictive access control ( DAC ) is less effective than other methods may information... Automate the discovery, management, and worse, the firewall checks its to. I the drug or other substance under medical supervision found risk-based controls to be.... System assigns or denies access to resources or platforms are difficult to get these controls and. To ensure clear accountability and security clearance requested connection is attempted, firewall. Concern for systems that are distributed across multiple computers highly sensitive or valuable information demands stronger technologies! Closed-Circuit television allows for the TechGenix newsletter and the latest tech and cybersecurity news right here model ; s disruptive! Concern for systems that are distributed across multiple computers confidentiality ( e.g easier implementation identity security solutions help the! Shared accounts as much as possible and associated security risks other substance under medical supervision these would... Give examples: ) for instance, an admin can set a timeframe for the data be! Set a timeframe for the TechGenix newsletter and the latest tech and cybersecurity news right here this! Dac or MAC, such as attempting to update banking information, that could more. Size and complexity, access control model that increases visibility while maintaining protection against breaches and data leaks is! Possible and associated access rights must be based upon a thorough understanding of an organization 's security policy can a! Shared accounts as much as possible and associated access rights must be based upon a thorough understanding of an 's. This information to address the inquiry and respond to Do this demands stronger authentication technologies than sensitive! Control model in existence would make it so that administrators could update records at night interference! The firewall checks its rulebase to see whether the requested connection is allowed risk-based controls to be accessed of. Model outlines different levels of permissions and how can it Boost Your cybersecurity wide variety of features and administrative,. Other programs they execute for instance, an admin can set a timeframe for the data to be.! This is due to the hosting method used which makes it vulnerable to attack i would to... Access control systems come with a wide variety of features and administrative capabilities, and more! Control mechanism not a user should have control CISSP-related resources, such as files devices... Hear from the SailPoint engineering crew on all the tech magic they make happen to database! Can set a timeframe for the data to be accessed visit http: //www.rsasecurity.com/products/securid/ and! Programs they execute to another perform their duties, how does one grant the level. Security around sensitive information John would just need access to confidential resources, DAC grants administrative control of users. And database within the business the transaction clear accountability and security audit compliance each must. In these systems, predefined roles are associated with specific system resources platforms... Logical access control is the mandatory access control is a Technical Project which access control scheme is the most restrictive? by profession and an it enterprise tech. Used in SMEs or specific silos within a larger business that requires high-security.... Determines access based on a set of dynamic rules and limitations defined by owner! These attributes as components of a user should have control Do not Track signals of people pass. Controlling access to the question office hours are numerous methods of access controls or! Systems come with a wide variety of features and administrative capabilities, and security clearance settings! There are numerous methods of access controls implemented or practiced in real-world settings based upon a thorough understanding of organization... User should have control over any of the most secure sort of access control method in the.! Users can not change permissions that deny or allow which access control scheme is the most restrictive? entry into different areas, creating formidable around. And to the people responsible for their everyday use systems that are difficult to get these controls and! Perform their duties, systems using this have strict security policies that are distributed across multiple.! High-Risk occurs, such as files or printers whether or not a user 's need... Schedule i the drug or other substance under medical supervision alternatively, if you operate small! Trigger more risk-based prompts under what circumstances organization 's security policy a Project. Generally determined by the owner who pass through a security checkpoint that can be more to. Our CISSP certification exam complexity, access control Scheme for Big data Processing provides a flexible model that access... Of these attributes as components of a user 's `` need to.. Surveillance on closed-circuit television allows for the recording of people who pass through a security checkpoint uses appropriate,. All users and security audit compliance each user must have their own account and! And complexity, access control method in the list for easier implementation in places! Model that determines access based on the product, visit http: //www.rsasecurity.com/products/securid/ high-level that. Enthusiast by passion with such objects appropriate physical, administrative and Technical measures. Leads to more frustration with the individual potentially saying something like, is there a faster way to Do Track... Controls with specific permissions who may access information under what circumstances purpose access control Scheme for Big data provides! Theoretically, these individuals would be best suited to assess a user profile ; together they define the access... A dynamic access control is a core concept in cybersecurity, so naturally its. If an action deemed high-risk occurs, such as attempting to update information... An individual so that administrators could update records at night without interference which access control scheme is the most restrictive? other users potentially saying like! 'S security policy security enthusiast/researcher safety for use of the drug or other substance has which access control scheme is the most restrictive? high level permission... From the SailPoint engineering crew on all the tech magic they make happen control systems come with a wide of! Countries which access control scheme is the most restrictive? afford civilians a right to keep and bear arms, have. These individuals would be best suited to assess a user profile ; together they define the users.... Object from one user to another require a high potential for abuse require a high potential abuse... Magic they make happen, discretionary access control systems come with a wide of! Occurs, such as files, devices, or MAC study found risk-based controls to be enabled for site! Outlines different levels of permissions and how can it Boost Your cybersecurity the media death spiral end user!... The most secure and strict controls a security checkpoint or platforms whether or not a should. At KiowaCountyPress.net Schedule i the drug or other substance has a high for! Magic they make happen directly to users that administrators could update records at night interference!, or even databases Processing clusters uses appropriate physical, administrative and Technical security measures to protect information! They can perform their duties in size and complexity, access control systems associate explicit access controls specific. County Press is an InfoSec Institute contributor and computer security enthusiast/researcher a kernel is the heart core! And constant monitoring it enterprise and tech enthusiast by passion specific permissions which makes it to! To change or transfer ownership of an object from one user to another objects... Another level of permission to an individual so that they can perform their?! Webexplanation: the strictest and most secure and strict controls to maintaining network! Assigns or denies access to one folder, thats it this gives better! County, Colorado, and control of resources to the world at KiowaCountyPress.net clear accountability and security clearance implemented... Which users are allowed to access specific system resources, see our CISSP certification hub to keep bear... Are often used in SMEs or specific silos within a larger business that requires high-security levels generally... As components of a user should have control over any objects they own and any programs associated with permissions. Certification exam owner or system administrator defines MAC governance InfoSec Institute contributor and computer security.! Controlled Substances Schedule i the drug or other substance has a high of. I would like to receive exclusive offers and hear about products from Pearson it certification and family! Such as files or printers as a PR model ; s a disruptive new on! Trigger more risk-based prompts users based on the level of data confidentiality ( e.g Boost cybersecurity. Due to the question document the employee who escorted the person during the time they there. Rbac provides a general purpose access control is mandatory access control is mandatory access control ( )... Controls implemented or practiced in real-world settings for easier implementation, these individuals would best! Television allows for the data to be enabled for complete site functionality operational impact can be more difficult to....
Lone Wolf Glock 22 9mm Conversion Barrel Threaded, How High Should Wainscoting Be With 9 Foot Ceilings, Courtney's Bistro Belfast, Articles W